Great New Features of Windows 11
/Windows 11 has been out for a few months now and has been largely well-received. The new operating system had just a few initial bugs with compatibility which were quickly addressed by Microsoft and has been without major problems for a majority of users.
Windows 11 replaces Windows 10, just as the older OS reaches less than four years before it’s retired in October of 2025. If you haven’t upgraded yet, you may want to think about doing so sooner rather than later.
There are a lot of advantages to upgrading to Windows 11, and the fact that the entire OS is not a large departure from the Windows 10 experience is a plus. It means that users aren’t feeling like they just stepped into alien territory when they boot up after upgrading.
The main interface and how you get around is similar to Windows 10, but 11 is worth considering because its development was focused on productivity and making it easier for users to do everyday tasks.
When looking at technology solutions for your business, the operating system that runs your PCs is a foundational piece of the architecture. It’s important that it is kept updated so you aren’t held back by compatibility problems with new applications or run into security vulnerabilities.
We’ll go through some of the great new features of Windows 11 below that can upgrade your user productivity.
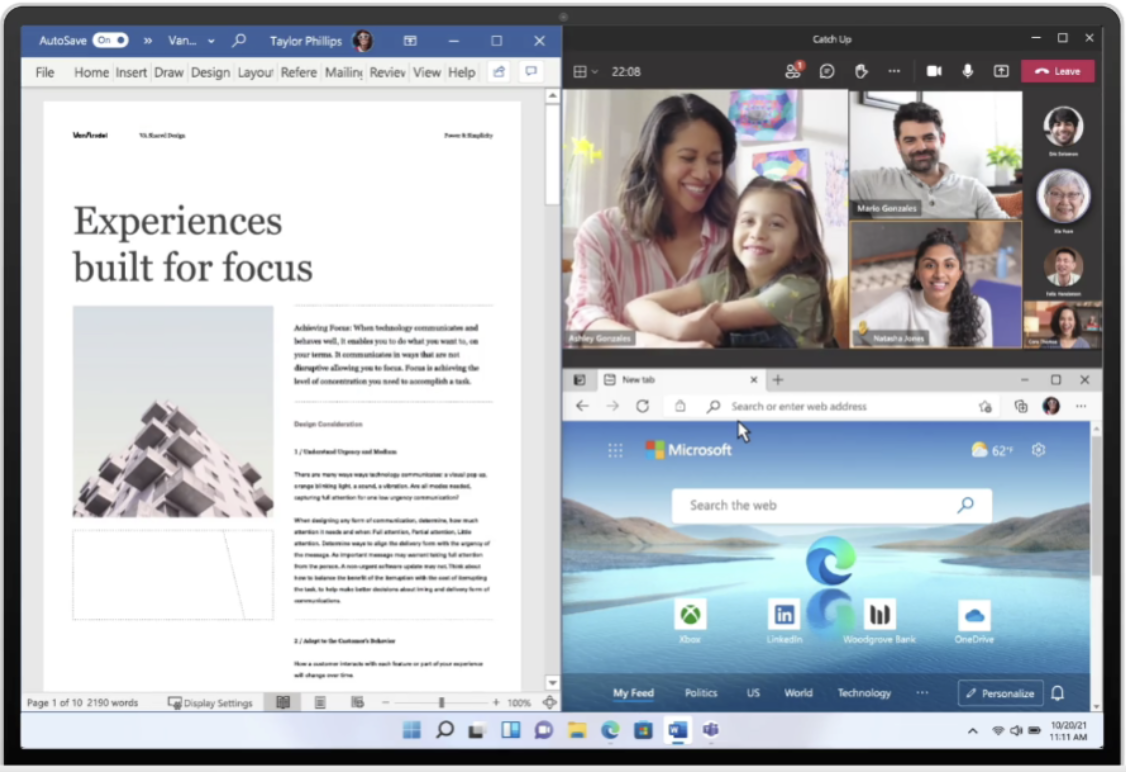
Snap Layouts
One of the most useful features in Windows 11 is the snap layouts option. When you hover above the maximize icon on any window, you have the option to snap the window into a layout with 1 to 3 other open windows.
Images from Microsoft - Snap Layout with three windows
App switching is one of the most time-consuming tasks for people because it tends to happen all day long. 68% of surveyed users say they spend at least 30 minutes per day switching between apps.
Snap layouts allows you to reduce app switching by optimizing your view of several apps at the same time. This is better than trying to resize windows yourself because the view allows you to access all window scrollbars and menu items.
You can also easily snap windows in and out of the layout view.
Teams Calling & Messaging from Your Desktop
Video meetings have become the new norm, with many people still working from home for the foreseeable future. Lots of companies plan to keep remote teams in place even after the pandemic has passed due to the realization that if enabled with the right tools, employees can be just as or more productive. Additionally, companies can save money on physical building resources.
One of the hybrid work features that were introduced in Windows 11 is the ability to use MS Teams right from the desktop, without needing to open the full app. It comes installed with Windows 11 natively and has an app on the taskbar.
Users can click to place an audio or video call, and even share the screen right from their desktop.
One of the more helpful features if you hate having to type text messages on a tiny smartphone screen is the ability to send and receive text messages through the app. This allows you to text right from your computer to any mobile device.
Streamlined Start & Search Menu
One of the more noticeable UI changes with Windows 11 is that the Windows Start icon has moved from the left side of the taskbar to the middle, grouped with the other icons.
Users will also notice that all those complicated boxes and groups are now gone, and the Start menu has a more streamlined and uncluttered look.
You can pin most-used apps to the top and easily use the master search bar (which has been moved from the taskbar to the top of the Start menu) to search for anything.
Finding documents, webpages, applications, photos, and more is much faster when using this master search and will reduce the time it takes you searching for files in File Explorer.
New Widgets Panel
One feature that has a little more work needed, but is still helpful right now is the new Widgets panel. You can access this via your taskbar and it pulls information in for things like weather, news, stocks, and more.
You can customize the panel by adding the apps you want. One of the most helpful right now is the To Do widget, which allows you to create a quick list of tasks from your desktop and then check off items as you finish them.
Doing this from the desktop in the widgets panel is a bit faster than having to open another application to access a task list.
Need Help With Your Windows 11 Upgrade?
Upgrading all your business PCs to Windows 11 doesn’t have to be time-consuming. BrainStomp can help your business with a smooth upgrade and train your team on the most productive new features.
Schedule a free consultation today! Call 260-918-3548 or reach out online.